Excerpt here…
This post is part of a series:
- Linux training with overthewire Part 1: Bandit 1-10
- Linux training with overthewire Part 2: Bandit 11-20
- Linux training with overthewire Part 3: Bandit 21-30
- Linux training with overthewire Part 4: Natas 1-10
- Linux training with overthewire Part 5: Natas 11-20
- Linux training with overthewire Part 6: Leviathan
- Linux training with overthewire Part 7: Krypton
Level 0 - base64 decode
http://overthewire.org/wargames/krypton/krypton0.html
$ echo 'S1JZUFRPTklTR1JFQVQ=' | base64 -d
KRYPTONISGREAT
Level 1 - ROT 13
ssh krypton1@krypton.labs.overthewire.org -p 2222
# KRYPTONISGREAT http://overthewire.org/wargames/krypton/krypton1.html
$ cd /krypton/krypton1 && ls
README krypton2
$ cat README
The password \for level 2 is in the file
'krypton2'. It is encrypted using a simple rotation called 'ROT13'.
$ cat krypton2 | tr 'A-Za-z' 'N-ZA-Mn-za-m'
LEVEL TWO PASSWORD ROTTEN
Note: Same as Bandit level 11
Level 2 - Caesar cypher
ssh krypton2@krypton.labs.overthewire.org -p 2222
# ROTTEN http://overthewire.org/wargames/krypton/krypton2.html
$ cd /krypton/krypton2 && ls
README encrypt keyfile.dat krypton3
$ cat README
This level contains an old form of cipher called a 'Caesar Cipher' in the file 'krypton3'.
2 ways:
- Caesar bruteforce on https://www.dcode.fr/caesar-cipher
- Use your brain and find how the binary works (preferred method):
$ cd $(mktemp -d) $ ln -s /krypton/krypton2/keyfile.dat && chmod 777 . $ echo "ABCDEFGHIJKLMNOPQRSTUVWXYZ" > alphabet $ /krypton/krypton2/encrypt alphabet && cat ciphertext MNOPQRSTUVWXYZABCDEFGHIJKLUse the same code as Level 1, with a slight change in the letters mapping:
$ cat /krypton/krypton2/krypton3 | tr 'A-Za-z' 'O-ZA-No-za-n' CAESARISEASY
See Caesar cipher on Wikipedia https://en.wikipedia.org/wiki/ROT13
Level 3 - Letters frequency analysis
ssh krypton3@krypton.labs.overthewire.org -p 2222
# CAESARISEASY http://overthewire.org/wargames/krypton/krypton3.html
First approach: bash only
$ cd /krypton/krypton3 && ls
HINT1 HINT2 README found1 found2 found3 krypton4
$ cd $(mktemp -d) && ln -s /krypton/krypton3/found1 && ln -s /krypton/krypton3/found2 && ln -s /krypton/krypton3/found3
$ alph="ABCDEFGHIJKLMNOPQRSTUVWXYZ"
In bash, for each letter of the $alph, count the occurence:
$ for((i=0 ; i<26 ; i++)); do exec cat found*|grep -o "${alph:$i:1}" |wc -c; done
110
492
# [...]
56
In the end, we’ll need to sort this output with sort, so we need to 0 pad in order for 56 to become 056:
$ for((i=0 ; i<26 ; i++)); do exec cat found*|grep -o "${alph:$i:1}" |wc -c | xargs printf "%03d " ; done
110
492
# [...]
056
Let’s add letters because we’re humans, not computers:
$ for((i=0 ; i<26 ; i++)); do exec cat found*|grep -o "${alph:$i:1}" |wc -c | xargs printf "%03d " && echo "${alph:$i:1}" ; done > frequency && cat frequency
110 A
492 B
# [...]
056 F
Sort it:
$ sort -r frequency
912 S
680 Q
602 J
514 U
# [...]
And compare with English letter frequency on Wikipedia
| Letter | Relative frequency in the English language | Letter frquency in krypton3 files |
|---|---|---|
| e | 12.702% | S |
| t | 9.256% | Q |
| a | 8.167% | J |
| o | 7.507% | U |
| i | 6.966% | B |
Buuuuuut after many tries, I couldn’t find it this way. I tried many alphabets from letterfrequency.org such as etaoinsrhldcumfpgwybvkxjqz (English) or eariotnslcudpmhgbfywkvxzjq (Oxford).
Second approach: JCrypTool
So I gave JCrypTool a shot, and it worked!
Start by a copy/paste of each found* file and the password, each one without space, but separated by a newline:
Go ahead and start the analysis with Analysis > Substitution analysis. Use the text from the editor as the source, and the English dictionnary as the reference text.
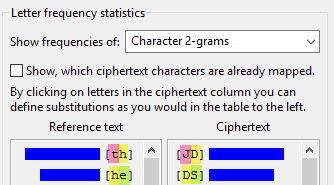
As we saw previously, we cannot rely on 1 letter analysis, so let’s try Bigrams. Open up the Character 2-grams analysis. The top 2 most frequent bigrams in English are [th] and [he]. In our texts, it’s [JD] and [DS]. Noticed the D?
Replace it and check the trigrams:
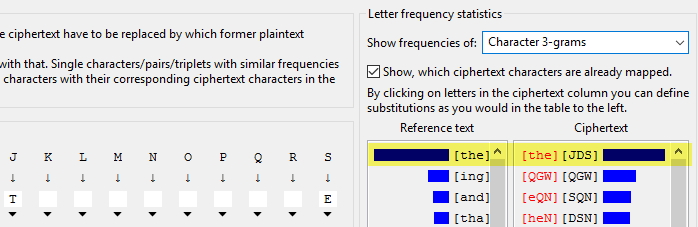
Great 😍
Get back to the bigrams again, let’s see what we can find. Maybe the [er] and [es]?
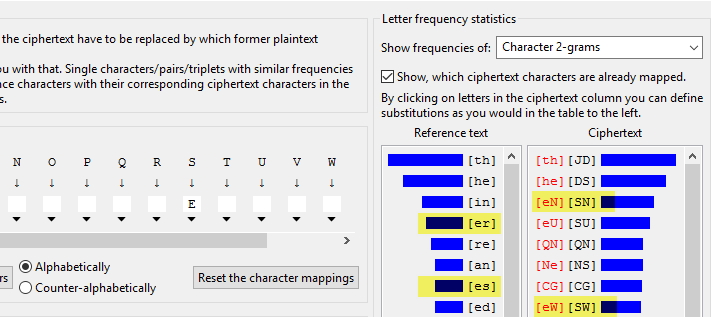
When replaced, it gives us 2 more trigrams: [her] and [ere]:
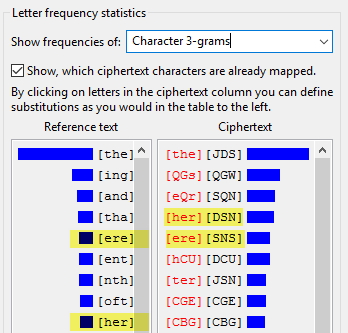
Proceed this way until you got the whole alphabet:
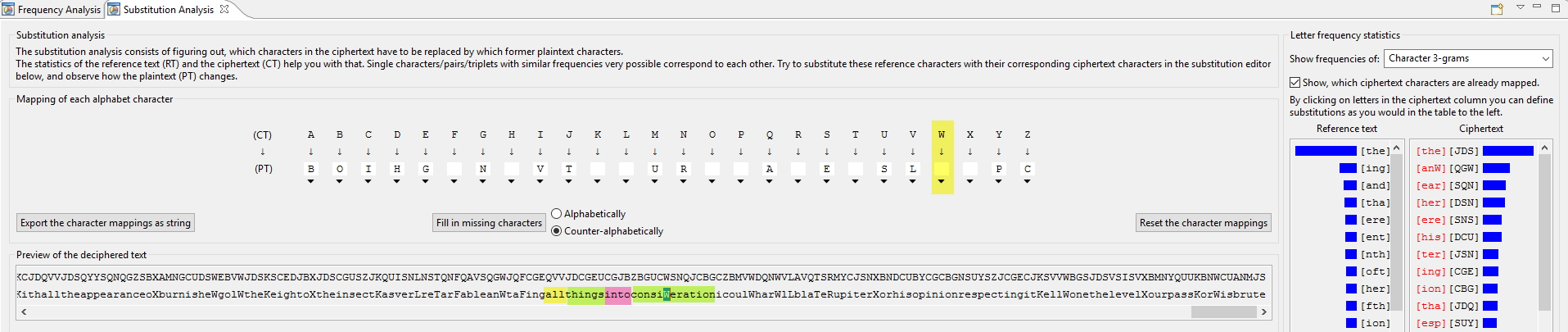
$ cat /krypton/krypton3/krypton4 | tr ABCDEFGHIJKLMNOPQRSTUVWXYZ BOIHGKNQVTWYURXZAJEMSLDFPC
WELLD ONETH ELEVE LFOUR PASSW ORDIS BRUTE
WELL DONE THE LEVEL FOUR PASSWORD IS BRUTE
Level 4 - Vigenère Cipher
ssh krypton4@krypton.labs.overthewire.org -p 2222
# BRUTE http://overthewire.org/wargames/krypton/krypton4.html
$ cd /krypton/krypton4 && ls
HINT README found1 found2 krypton5
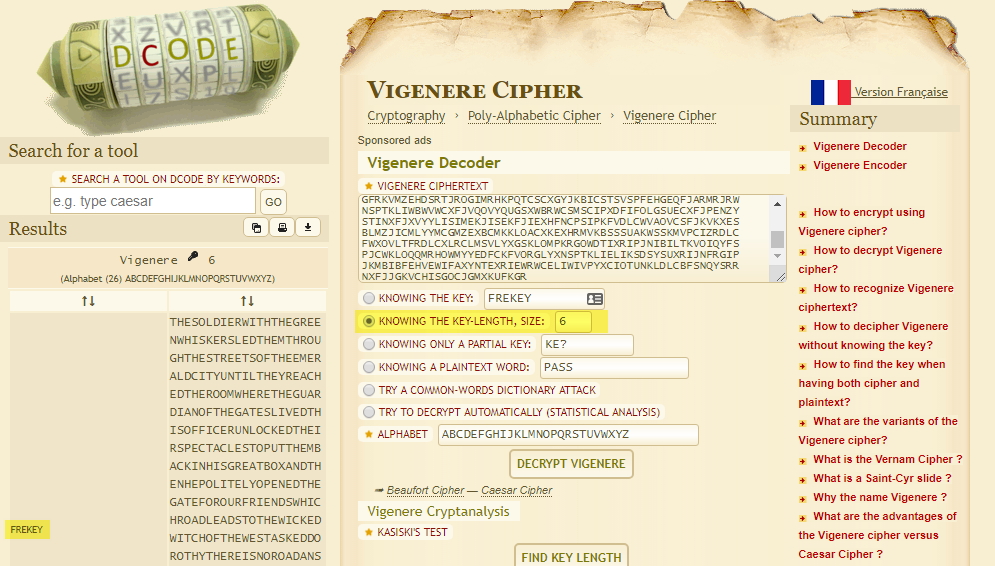
- Key:
FREKEY - Encoded pass:
HCIKVRJOX - Decoded pass:
CLEARTEXT
Level 5 -
ssh krypton5@krypton.labs.overthewire.org -p 2222
# CLEARTEXT http://overthewire.org/wargames/krypton/krypton5.html
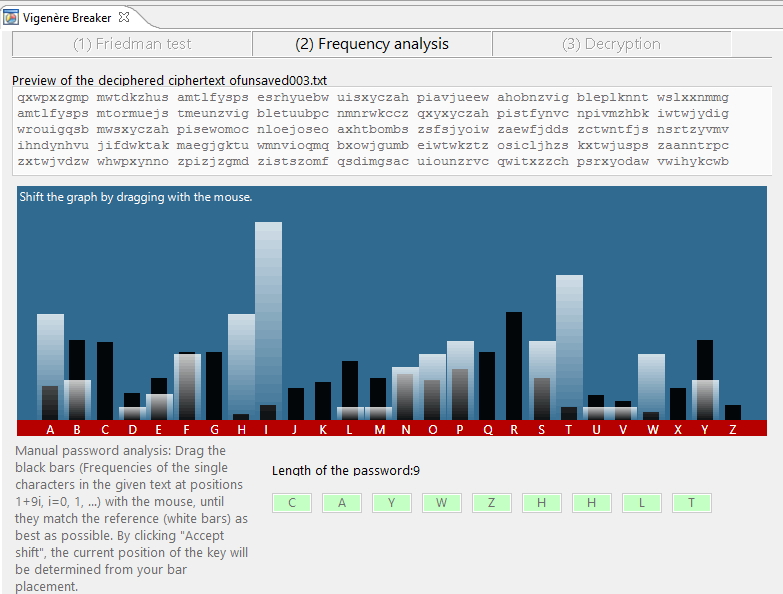
Viegenere breaker in JCrypTool:
This post is part of a series: